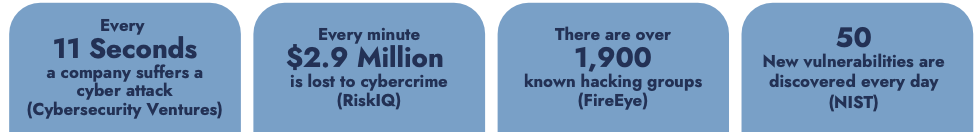
Attack Surface Management
Understand and Secure Your Digital Exposure
In the evolving landscape of cybersecurity, it's crucial to identify and manage all potential entry points that adversaries might exploit. Our Attack Surface Management service provides a comprehensive view of your organization's external vulnerabilities, enabling proactive defense strategies.
Continuous vs. One-Time Attack Surface Assessment
Need a quick look at your attack surface to check your security?
You can perform a one-time assessment and receive a report quickly to give you peace of mind. With new vulnerabilities being discovered daily and the never-ending wave of cyber-attacks, your attack surface changes constantly.
Continuous Attack Surface Assessment using the Integrated Cybersecurity Engine is a cost effective way to keep up with the latest vulnerabilities and threats and manage your exposure.
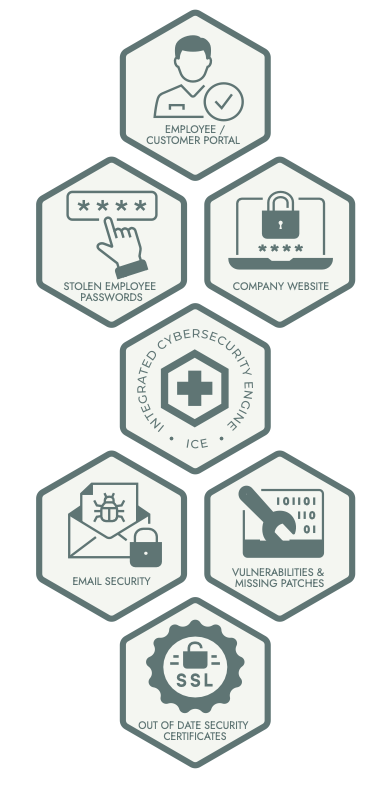
Key Features of a Surface Assessment
- Comprehensive Asset Discovery: Identify all internet-facing assets, including shadow IT and forgotten subdomains, to ensure no exposure goes unnoticed.
- Continuous Monitoring: Stay ahead of emerging threats with real-time surveillance of your attack surface, promptly detecting changes and vulnerabilities.
- Risk Prioritization: Assess and rank vulnerabilities based on potential impact, allowing for efficient allocation of remediation resources.
- Actionable Insights: Receive detailed reports with clear remediation steps to strengthen your security posture effectively.
Benefits of a Surface Assessment
- Proactive Defense: By understanding your attack surface, you can anticipate and mitigate threats before they materialize.
- Regulatory Compliance: Maintain adherence to industry standards by identifying and addressing security gaps.
- Resource Optimization: Focus your security efforts where they are needed most, enhancing efficiency and effectiveness.
Don't wait for your business to become another cybersecurity headline