Concierge Cybersecurity
At ICE Cybersecurity, we specialize in analyzing and managing your organization's cybersecurity risks and compliance requirements, allowing you to focus on achieving your business objectives. With tailored security solutions delivered at the right time and investment, you can confidently engage with customers, auditors, stakeholders, and handle security incidents, knowing your business is well-prepared.
Your Cybersecurity Force Multiplier
ICE, the Integrated Cybersecurity Engine, serves as your cybersecurity force multiplier. By leveraging our proprietary blend of integration, automation, and analytics, we enable your team to dedicate more time to reducing risks. Elevate your security posture immediately with ICE.






Comprehensive Security Layer
People
Our team of experts rapidly assesses, remediates, and manages your cybersecurity program. With decades of experience in cybersecurity, audit, development, business, and IT, combined with a passion for innovation, we are dedicated to securing your business.
Process
Efficient, practical, and effective security processes are embedded in our DNA and the ICE Platform. We assist you in implementing a security program that aligns with your company's size, complexity, and compliance environment.

Platform
Designed with flexibility in mind, we assemble the right tools at the right time for the right investment. Our product-agnostic approach and management platform accelerate implementation, reduce costs, and eliminate vendor lock-in.
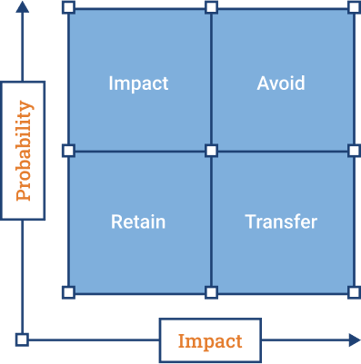
IT Risk Management
Identify, classify, and manage risks effectively. ICE collaborates with your team to determine risk areas, tolerance levels, and budget constraints, building a roadmap to mitigate potential impacts that concern you. This may involve training your employees, connecting you with insurance brokers, developing contingency plans, or helping you avoid risks altogether.
ICE ARMs Your Company
ICE equips your company with a comprehensive security
program to protect your business through a simple process:
program to protect your business through a simple process:
A
Assess
Begin by understanding your security drivers and assess your organization against relevant standards, best practices, and regulations. We don't just identify flaws; we provide solutions on a roadmap that fits your business.
R
Remediate
Recognize that not all gaps can or should be fixed simultaneously. The key is knowing which risks to address at the right time. Our platform and team help optimize your time and budget to maximize your security return on investment.
M
Manage
Maintain visibility, accountability, and control. Our platform keeps your security program tuned and continuously monitors for risks that could harm your business. Stay informed about your security program, demonstrate compliance, and manage your risk effectively.
"ICE helps identify, reduce and manage risk across our insurance portfolio."
Jeff Stull, CEO FusionMGA

Ready to get started?
We recommend beginning with an attack surface assessment. This evaluation identifies vulnerabilities and highlights areas where we can enhance your company's security and confidence.